The Intranet is Dead 1
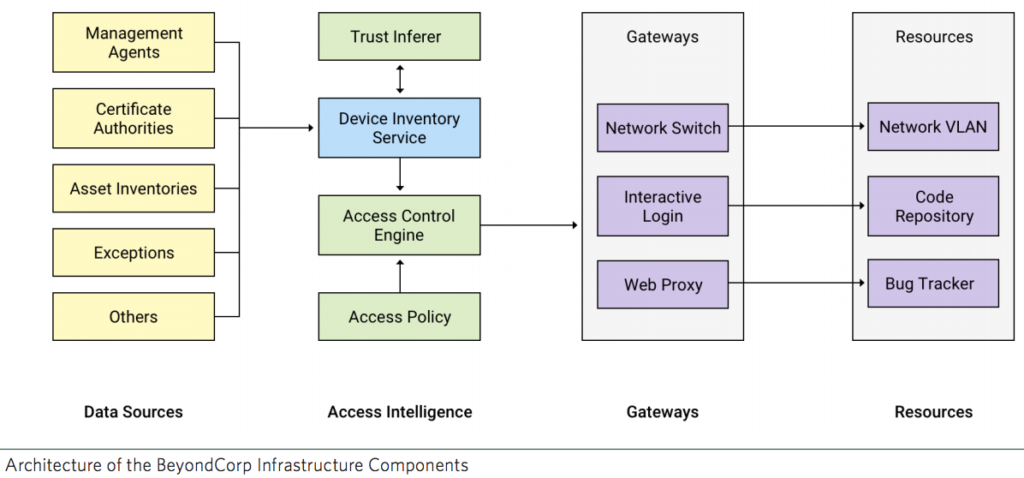
Architecutre of Infrastructure Components at BeyondCorp
Once we know something, we get accustomed to it, we start trusting it. I think this goes back centuries, when Romans said, “The best way to ensure peace is to be ready for war”. The security architecture has taken the same philosophy forward, “The best way to ensure Security, is to Trust no one”. The goal of Google’s BeyondCorp initiative is to improve our security with regard to how employees and devices access internal applications. Unlike the conventional perimeter security model, BeyondCorp doesn’t gate access to services and tools based on a user’s physical location or the originating network; instead, access policies are based on information about a device, its state, and its associated user.
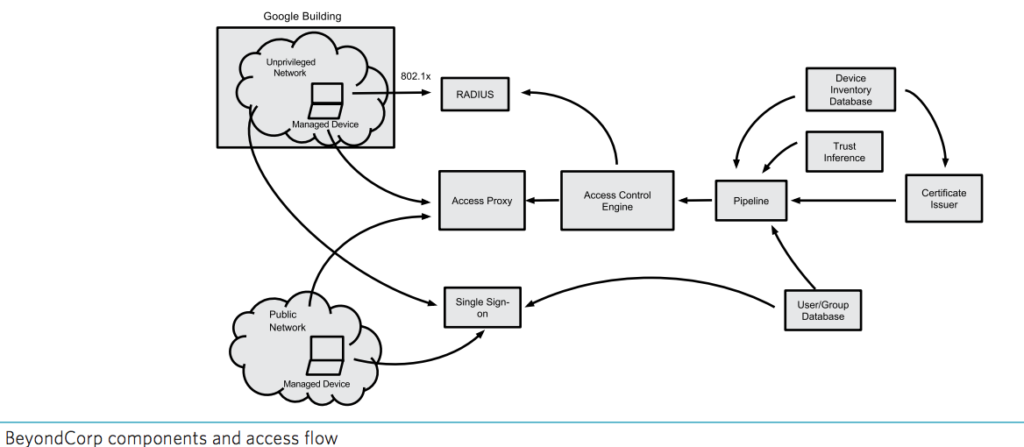
BeyondCorp Access Flow
Virtually every company today uses firewalls to enforce perimeter security. However, this security model is problematic because, when that perimeter is breached, an attacker has relatively easy access to a company’s privileged intranet. As companies adopt mobile and cloud technologies, the perimeter is becoming increasingly difficult to enforce. Google is taking a different approach to network security. We are removing the requirement for a privileged intranet and moving our corporate applications to the Internet. 2. Google’s BeyondCorp initiative is moving to a new model that dispenses with a privileged corporate network. Instead, access depends solely on device and user credentials, regardless of a user’s network location—be it an enterprise location, a home network, or a hotel or coffee shop. All access to enterprise resources is fully authenticated, fully authorized, and fully encrypted based upon device state and user credentials.
We can, with new thinking, enforce fine-grained access to different parts of enterprise resources. The reasoning goes at every level of security implementation, every component, every access, every user, there is absolutely no trust. Every entry and access must confirm the identity and validity of access. These kind of implementations are also important for cloud migration of systems. Using this newer security architecture thought process, we are losing the concept of Intranet, and security zones.
Security by Design, never by Implementation. 3
Christopher Reilly makes a very important point in security architecture, attempting to defend the attacks and techniques of today and tomorrow with the tools and processes of yesterday will simply not yield the effectiveness required to keep any data or systems secure. This is the very basis of our conclusion that now, more than ever before, there is a need for a new IT security architecture. We need a new way to think, some people argue we need to think like hackers. Every employee of an organization (small or large) has to think like a Security Architect. The security is everybody’s business. In the blog the security survey revealed,
- 53% of respondents felt that the need for a unified view of users across the enterprise was the #1 goal of a new IT security framework in their organization.
- 69% of respondents felt that some of their organization’s existing security solutions are outdated and inadequate.
- 59% of respondents felt that in their organization, employees and third parties bypass security policies and technologies because they are too complex.
- 77% of respondents felt that Machine Learning was one of the most important technology trends to reduce security risks.
- 72% of respondents felt that an improvement in staffing is a business goal that improves security posture.
It is amazing to know 77% people thought Machine Learning can reduce security risks. One thing to note, machine learning can be as good as the what we taught machines. A bad security practice can be learned by machines will create more than life security loophole. We will be trusting the system to protect itself. Offloading the “Thought Process” or “Implementation” heavy-lifting to machines is changing trust, trusting machines to protect themselves in my view is lazy, what do you think?
Security is always best if it is by Design, it cannot be by the implementation. Trusting the implementation platforms to provide robust security is proven myth, has been proven wrong over and over. It is time to create security by business strategy and adhered by everyone.
Connected Everything – Another security challenge 4
There appeared to be widespread agreement that companies developing IoT products should implement reasonable security. Of course, what constitutes reasonable security for a given device will depend on a number of factors, including the amount and sensitivity of data collected and the costs of remedying the security vulnerabilities. The Security Risk is exponentially related to the number of connections. More the connections, better the security policies need to be. If every device is network capable and has ability to influence its own domain, it will be imperative that the security cannot be reasonable, it needs to proportional to its connections and domain of their authority. 5. As to risks, participants noted that the IoT presents a variety of potential security risks that could be exploited to harm consumers by: (1) enabling unauthorized access and misuse of personal information; (2) facilitating attacks on other systems; and (3) creating risks to personal safety. Participants also noted that privacy risks may flow from the collection of personal information, habits, locations, and physical conditions over time. In particular, some panelists noted that companies might use this data to make credit, insurance, and employment decisions. Others noted that perceived risks to privacy and security, even if not realized, could undermine the consumer confidence necessary for the technologies to meet their full potential, and may result in less widespread adoption.
Software-Defined Networking (SDN) is an emerging strategy to increase the functionality of the network connected devices, reducing operating costs, reducing complexity and enabling innovation. SDN architecture models have three layers: (1) an infrastructure layer consists of network devices (e.g., switches, routers, virtual switches, wireless access point), (2) a control layer consists of SDN controller(s) (e.g., Floodlight, Beacon, POX, NOX, MUL, Open daylight, etc.) and (3) an application layer that includes the applications for configuring the SDN (e.g., Access control, traffic/security monitoring, energy-efficient networking, management of the network).
One important feature of SDN architecture is its ability to extends the security perimeter to the network access end point devices (access switches, wireless access points, etc.), by setting up security policy rules to network devices. The next generation Internet architecture, requires elevated security levels, such as authenticating network devices, users and objects connecting each other Furthermore, we need to monitor the behavior of both the users and the objects, establish trust boundaries, and use accounting methods along with software verification. There are always more ways to solve a problem, but in security realm, there is always one and only one correct solution, a solution that is secure. In coming times, there will be so many different emergent security architecture will suggest different approaches. It will be a while before industry will settle on one. Every security solution can and will be hacked, we just need to upgrade out of it before hackers can get to it.
References
- Osborn, B., McWilliams J., Bayer B., Saltonstall, M., BeyondCorp – Design to Deployment at Google, Google Research, Vol. 41 (2016), pp. 28-34. Available at https://research.google.com/pubs/pub44860.html
- Ward, R., Beyer B., BeyondCorp: A New Approach to Enterprise Security, Google Research, Vol. 39, No. 6 (2014), pp. 6-11, Available at: https://research.google.com/pubs/pub43231.html
- Reilly, C., 2017, The Need For A New IT Security Architecture: Global Study On The Risk Of Outdated Technologies, Citrix Blog, Available at : https://www.citrix.com/blogs/2017/02/07/the-need-for-a-new-it-security-architecture-global-study-on-the-risk-of-outdated-technologies/
- Flauzac, O., Gonzalez C., Nolot F., 2015, New Security Architecture for IoT Network, Procedia Computer Science 52 ( 2015 ) 1028 – 1033
- FTC Report, Internet Of Things, Privacy and Security of Connected World
